Employee Safety During Times of Crisis
2020 has been nothing short of a year full of uncertainty and crisis. During times like this, employee safety must remain your first priority. Here’s...
Learn a few simple ways to protect your identity while using social media platforms.

It’s estimated that of the 7.91 billion people in the world, 4.95 billion are active internet users and 93.4% of those internet users (or around 4.62 billion) use the internet to gain access to social media platforms. And, as with anything else, when large groups of people are participating in an activity, there will always be people interested in doing nefarious things—like doxing people to gain access to their personal information for whatever reason.
If you’re not familiar with doxing, it’s when someone reveals your personal information online (like your full name, address, and place of work) without your consent. Unlike hacking where the intent is usually theft of some kind and requires gaining access to a person’s online accounts and/or personal files, doxing is usually done to embarrass someone or in retaliation for perceived wrongdoing and it’s incredibly easy to do.
In this article, we’re going to talk about how the information we share on social media platforms can become fodder for those interested in nefarious activities as well as several things that we can do to protect ourselves while still enjoying social media.
Everything we post online provides “clues” about who we are, especially when we post pictures to our social media accounts. What you might think is a harmless picture of our pet snoozing on the couch could actually provide enough information for someone to locate you.
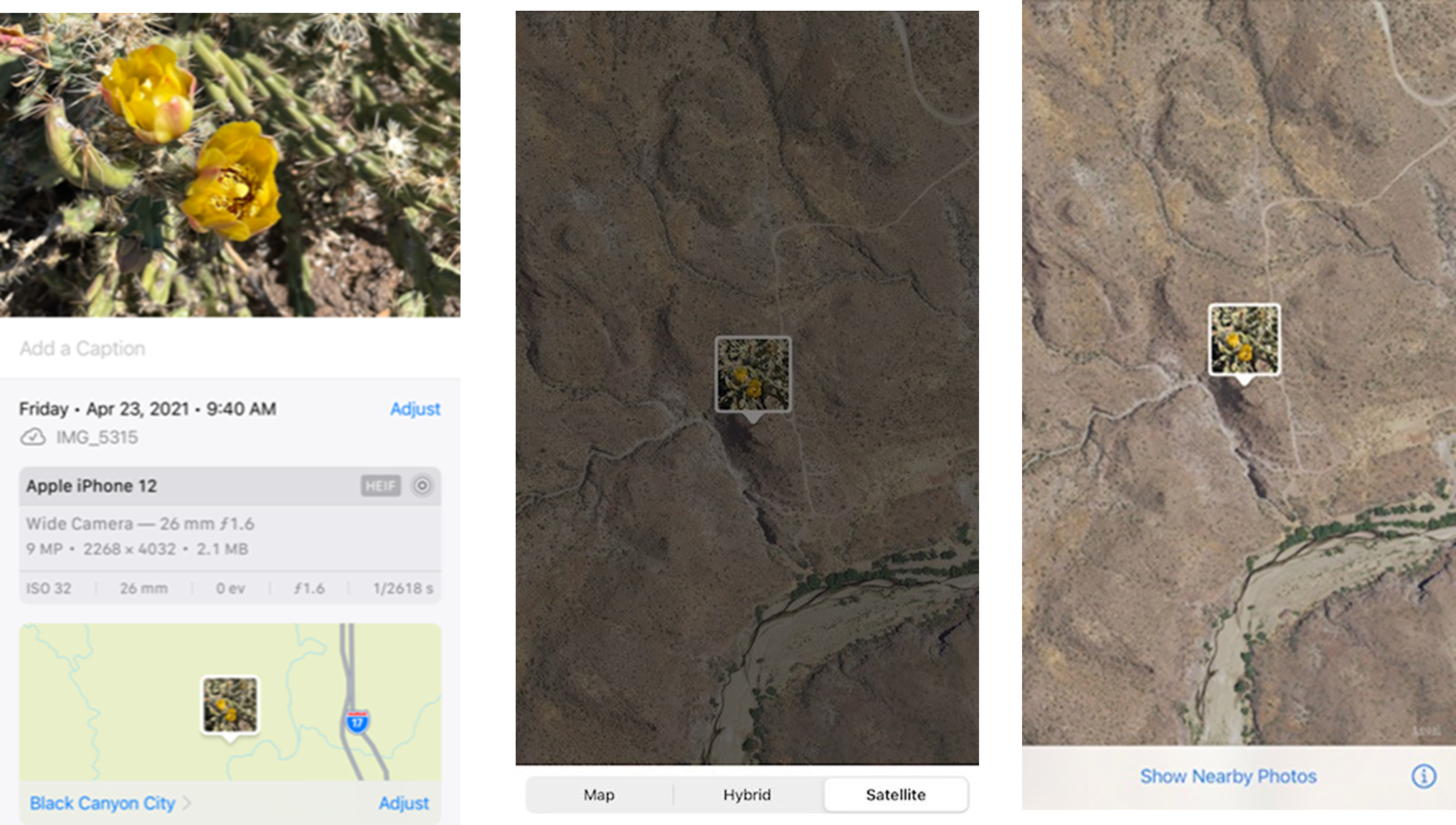
 Every time you take a picture with your smartphone, it captures quite a lot of information called “metadata” about the photo that you might not be aware of. For example, the picture below was taken with an iPhone during a vacation in Arizona. To most people, it looks like a picture of a flowering cactus. But, there’s quite a lot of other information included in this photo if you know where and how to look.
Every time you take a picture with your smartphone, it captures quite a lot of information called “metadata” about the photo that you might not be aware of. For example, the picture below was taken with an iPhone during a vacation in Arizona. To most people, it looks like a picture of a flowering cactus. But, there’s quite a lot of other information included in this photo if you know where and how to look.
Upon closer examination, this photo includes basic information like when it was taken and the type of camera phone used to take it—but it also includes much more detailed information. Because the location settings were enabled when the picture was taken, this photo also includes the exact location where the photo was taken and even offers the ability to see that location on a map or using satellite imaging.
While these features can be helpful at times, it’s important to know they’re there and how to turn them off when necessary. Luckily managing these features isn’t difficult and can be done by following the instructions found in this CNET article for iPhones and this article from Net Quest for Android phones.
Another way a person’s pictures can reveal more about them, like their actual identity, is when a person uses the same photo across several social media accounts. You may not realize this but every picture has a specific arrangement of pixels (a lot like fingerprints) and the odds that two pictures will have the same exact pixel arrangement are extremely slim. Because of this, websites and apps dedicated to performing what’s called a “reverse image search” make it possible for someone to save a picture from social media and then search for where else this picture might have been used.
If someone has used the same profile photo for several social media accounts, has posted the same picture in multiple locations, or has used a specific photo for professional publications or some such, the chances of being identified through this method are increased. When a photo is found using a reverse image search, it may reveal things like who the person is, where they work and who their friends and family are. This bit of information may also be exactly what someone intent on doxing another person needs to verify someone’s identity. In other words, when a found photo is tied to multiple different social media accounts for the same person, it’s like hitting the doxing jackpot.
So, how do you keep from being found through this method? One sure-fire way to avoid this is by not using your real photo for any social media accounts and by making your social media accounts private. If that’s not appealing to you, at least do yourself a favor and use different profile photos for different social media accounts and no matter what, never use your LinkedIn profile photo for any other social media type accounts. Doing so is just asking for trouble.
Yet another way your photos can be revealed is by what else is in your photos when you share them. Anything that can be enhanced in your photos that could reveal who you are, where you might work or your exact location is something you should keep private.
The best way of preventing your photos from revealing much about you is by blurting out things in the background you don’t want others to see or by making sure that what you post isn’t accidentally giving someone enough information about you to tie you to a specific place, like a college or place of business. Because, once someone has a little bit of information like this, it becomes much easier to find you.
So, before you post that picture of your pet snoozing on the couch or a photo from your most recent work conference, take a few minutes and look at the picture to make sure there’s not enough information in the photo itself or in the photo’s file data that might reveal too much about you.
Social media platforms should always be used with a certain amount of caution, even if we’re only sharing information with people that we know personally or professionally. While you may know everyone you share things with, every one of those people also has a network of people they share information with. And, for many social media sites, sharing information with people you’re networked with or “friends” with means everyone they’re friends with can often see what you’re posting.
Aside from never sharing personal information on social media, another good way to reduce the amount of information that can be shared with those outside your network is by managing the privacy settings for your social media accounts. For example, certain social media sites will allow you to keep many things private such as your friends' list, your life history (workplaces, schools, etc.) and some even allow you to prevent those who are outside your network from seeing what you post. No matter what, it’s always a good idea to perform regular “privacy checkups” on every social media platform you use to make sure that the settings haven’t been updated or changed without your knowledge.
Every device connected to the internet uses an Internet Protocol address or IP address to communicate with other devices and websites and to receive information from them. Think of it as a physical address for your device. If you were to order an item from a company online, you’d have to supply your physical address so the company would know where to send the package, right? Well, your IP address is very similar in the sense that when you visit a website, you’re essentially requesting information from that website to be sent to your device and without the IP address the website would have no way of knowing where to send it.
While there are billions of IP addresses out there, the ones attached to your devices are generally unique to each device making them another method that can be used to locate you. This information is often much more difficult to locate than the private information in your pictures, but even so, it’s a good idea to add a layer of protection just in case.
One way to do that is by using what’s called a Virtual Private Network or VPN which masks your IP address making it much less detectable to those looking for it. VPNs are especially useful at providing protection for your IP address while logged on to the free public Wi-Fi at places like coffee shops and in airports and hotels, among other public places. Depending on the VPN service being used, there may be additional included benefits offered such as receiving alerts when your data has been involved in a leak and features that block malware, ads, and trackers. If you’re interested in learning more about VPNs and what to look for when choosing one, check out this article from VPN Mentor.
It’s true that social media can be a great tool for meeting like-minded people, expanding a business or even locating your next job, but it can also be a dangerous place if you’re not careful. But, by protecting your devices and by maintaining your social media accounts through performing regular reviews of what you’ve shared, limiting what information is available, and performing regular privacy checkups you can help make sure your private information stays private and keep from falling victim to someone intent on revealing your identity for nefarious reasons.
2020 has been nothing short of a year full of uncertainty and crisis. During times like this, employee safety must remain your first priority. Here’s...
Here's what you should consider when you are interviewing for a safety role. Hint: ask about the company's safety culture.
Learn about what’s required to be in every confined space permit and how to keep the entire entry process organized.
Subscribe to our blog and receive updates on what’s new in the world of EHS, our software and other related topics.